Mature GRC lacks innovation, while the birth of modern GRC is driven by corporate scandals and regulatory events. In 2000, OneTrust entered the GRC market through GDPR, capturing the market for GDPR and other privacy framework automation. By 2018, OneTrust had become a dominant player in the GRC market.
In the late 1990s and early 2000s, platforms like Archer and Metricstream were the first to automate GRC workflows and store GRC information. Vanta and Drata launched in 2016, offering SOC 2 in a box. These solutions applied modern UX and workflows to legacy processes, making SOC 2 accessible to everyone.
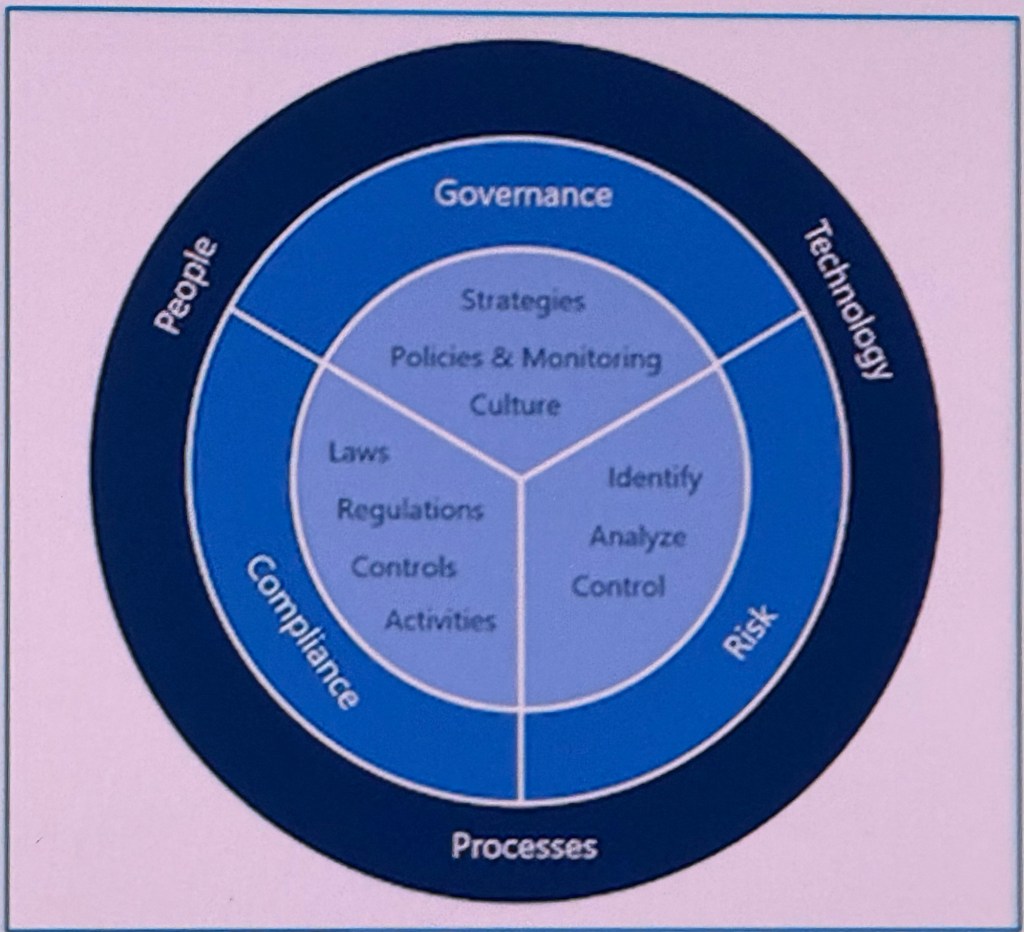
GRC stands for Governance, Risk, and Compliance. It’s a structured framework that helps organisations align IT with business goals, manage risks, and meet regulatory and industry requirements.
Governance establishes rules, policies, and operations that guide a company’s business goals. It defines responsibilities for key stakeholders like the board of directors and senior management.
Risk management helps businesses identify, assess, and mitigate potential risks that could hinder objectives. It prioritises what matters most and focuses resources accordingly.
Compliance involves adhering to rules, regulations, and standards, both external and internal.
Compliance requirements differ based on industry and data storage location, especially sensitive data like PII. For instance, US healthcare companies must comply with HIPAA, while those storing data on European citizens must adhere to GDPR. Data storage location impacts compliance, with interpretations varying by region.
GDPR enforcement can differ based on data storage location. For example, storing EU citizen data in Germany may subject a company to strict regulations. Many UK companies store PII data in Canada to avoid strict GDPR interpretations. Understanding data localization is crucial for compliance.
Identify the industry and location of stored data, especially PII or sensitive information. Assess the criticality of data assets and potential impacts in case of data loss. Companies must prioritise compliance to mitigate risks effectively, regardless of the data type.
Governance sets the direction, risk management identifies and addresses obstacles, and compliance ensures that all activities are within legal and regulatory boundaries.
For instance, a European company named ABC must comply with GDPR. If ABC has operations in India, employees accessing EU data must also comply. To achieve this, ABC appoints a data protection professional who creates policies and strategies (governance). A risk assessment identifies gaps in compliance, and compliance is demonstrated by providing evidence like reports showing adherence to GDPR requirements. Policies like restricting pen drive use or limiting data downloads ensure compliance across people, processes, and technology.
Organisations typically adopt a top-down approach. The CEO sets the business strategy, the CIO develops the IT strategy, and the CISO formulates the information security strategy to support IT and business objectives. Security managers create tactical plans, and administrators implement operational plans. This hierarchy ensures alignment from top to bottom, supporting effective governance.
Measurement is done through metrics and compliance assessments. For instance, if an incident management system is implemented, metrics might include incident resolution counts, response times, and user satisfaction. Regular reviews and gap assessments help determine if objectives are met and where improvements are needed. This feedback loop ensures continuous improvement in governance.
Begin by understanding business requirements and stakeholder interests. Develop a clear information security strategy aligned with business objectives. Create relevant policies, assign responsibilities using frameworks like RACI, conduct risk and gap assessments, and establish measurable programs. Regularly review and update these elements based on business impact and changing risks to ensure effective governance.
Shadow Risk Acceptance
GRC teams should help manage risk, not create it.
Risk Management: Do we manage risk or compliance?
Explicit vs. Implicit Risk Acceptance: Unknown unknowns
• Organisational Risk
• Overburdened SMEs
• Dissatisfied Partners
• Unmet expectations
Who knows everything about everything?
Practical Examples:
– GRC Benefits: Questionnaire automation, audit readiness and evidence gathering, rapid onboarding of new standards, continuous control monitoring and assurance, and knowledge retention.
– Outside of GRC Benefits: Security: Tabletop exercise, DevOps: New product feature, Legal: Contract review, IA: Operational Risk Assessment, M&A: Acquisition Integration.
Alignment with GRC is crucial for achieving both qualitative and quantitative leaps.
GRC problems align with Al’s strengths:
– Constant internal and external changes necessitate proactive risk and compliance measures.
– Complexities and requirements are increasing faster than team capacity, requiring effective management to reduce response times from weeks to hours.
– GRC teams are expected to possess complete organizational knowledge within hours, enhancing clarity and readiness.
– “Continuous Compliance” is often unrealistic or even non-existent for most companies, but Control Assurance delivers trust internally and externally.
– Traditional automation struggles to handle GRC’s complexity, while continuous control monitoring is feasible.
What Can Happen:
• Enable proactive risk and compliance management.
• Reduce response times from weeks to hours.
• Enhance clarity and readiness (Control Assurance).
• Foster trust internally and externally.
• Enable continuous control monitoring.
AI for GRC signifies a fundamental transformation in how various GRC roles are executed. It is characterized by five core criteria: being embedded in essential GRC workflows, designed specifically for GRC, intelligent rather than merely automated, based on real operational data, and transparent and accurate.
GRC helps organizations reduce risk and improve compliance effectiveness.
Governance: The rules, practices, and processes an organization uses to direct and control its activities.
Risk management: The process of identifying, assessing, and responding to threats or events that can impact company or customer objectives.
Compliance: The country/region, state or federal laws or even multinational regulations that an organization must follow.
Authentication (AuthN) is the process of verifying a person’s identity to grant access to resources. Authorisation (AuthZ) determines the level of access or permissions granted to authenticated users.
Identity has emerged as the primary security perimeter for organisations, allowing them to protect their assets. It involves verifying and authenticating individuals or entities, which can include users, applications, devices, and other entities. The identity infrastructure is supported by four key pillars: administration, authentication, authorisation, and auditing. This approach is applicable to various components such as cloud applications, employees, on-premises applications, and devices.
Modern authentication encompasses authentication and authorisation methods between clients and servers.
At the heart of modern authentication lies the identity provider (IdP).
IdPs offer authentication, authorisation, and auditing services.
They enable organisations to establish authentication and authorisation policies, monitor user behaviour, and more.
Key capabilities of an IdP and “modern authentication” include support for secure authentication methods, single sign-on, federation with other IdPs, and more.
Concept of directory services
Directory services store directory data and make it accessible to network users, administrators, services, and applications. A directory is a hierarchical structure that stores information about network objects.
The most well-known directory service is Active Directory Domain Services (AD DS), a central component in organisations with on-premises IT infrastructure. Microsoft Entra ID is an evolution of identity and access management solutions, providing organisations with an identity as a service (IDaaS) solution for all their applications across cloud and on-premises.
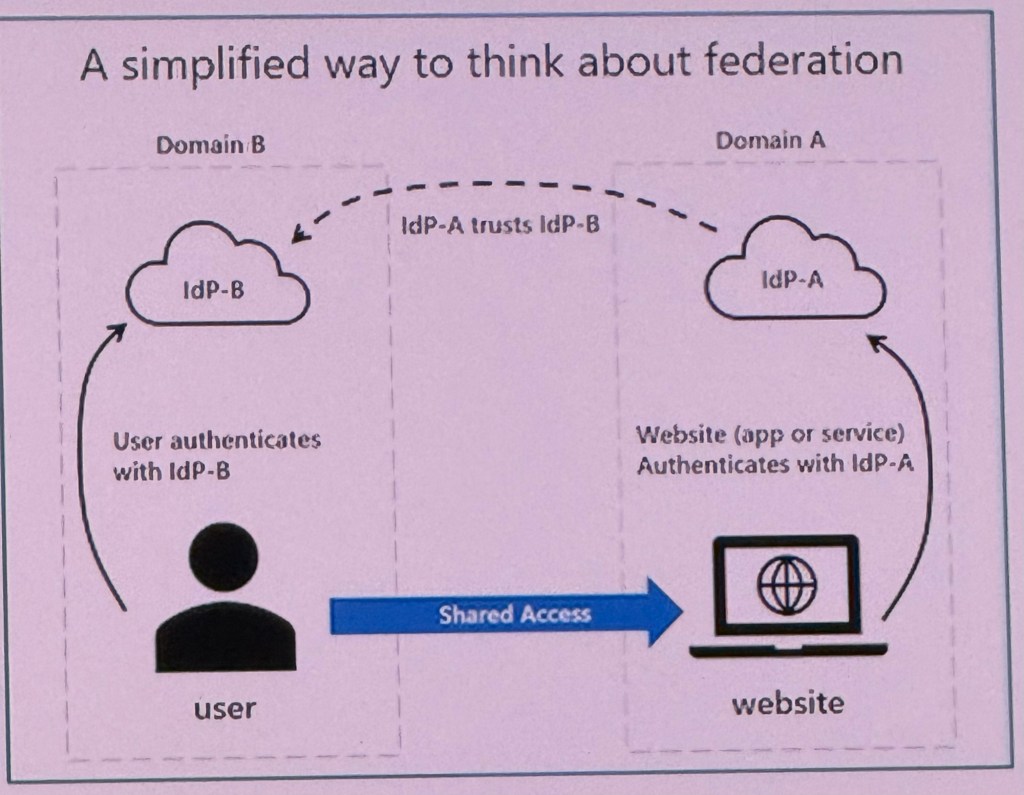
Federal authentication
The website uses the authentication services of Identity Provider A (IdP-A). The user authenticates with Identity Provider B (IdP-B). IdP-A has a trust relationship configured with IdP-B. When the user signs in to the website, the website can trust their credentials and allow access.