Why Does Digital Trust Matter?
High levels of digital trust lead to several benefits:
– Positive reputation
– More reliable data for decision-making
– Fewer privacy breaches
– Fewer cybersecurity incidents
– Stronger customer loyalty
– Faster innovation due to confidence in technology/systems
– Higher revenue
Low levels of digital trust, on the other hand, often result in the following consequences:
– Reputation decline
– More cybersecurity incidents
– More privacy breaches
– Loss of customers
– Less reliable data for decision-making
– Negative impact on revenue
– Slower ability to innovate
Introduction
Digital trust refers to the confidence individuals and organisations have in the integrity of relationships, interactions, and transactions within a digital ecosystem. It encompasses the ability of people, processes, information, and technology to create and maintain a trustworthy digital environment.
Given the ubiquity of technology in all aspects of life, most organisations and individuals rely on and utilise digital products and services. However, many people and businesses overlook the crucial role of trust between providers and consumers. Trust is a fundamental condition that enables parties to make decisions with confidence.
To fully understand digital trust within the context of the digital ecosystem, it is essential to expand its definition.
Digital Trust Context
Digital Evolution
Digital transformation integrates digital technology into all business areas. Enterprises must reevaluate their technology use, people, and processes to create new revenue streams. This requires challenging antiquated thinking with a cultural element that encourages experimentation and embraces failure.
Digital trust is crucial for competitive advantage. Companies must reassess how customers and users perceive them as the digital evolution phenomenon meets their changing expectations.
Digital trust, unlike conventional trust, emphasises integrity and adherence to moral values. It encompasses relationships, interactions, and transactions in various situations and exchange frequencies.
Digital trust considers the entire ecosystem, while confidence typically focusses on the relationship between two entities.
Digital Trust Context
Consequences of Digital Trust Deficiencies
A business can lose its trustworthiness in the digital realm for various reasons. For instance, if the relationships between parties involved in transactions or interactions lack trust, confidence in the arrangement begins to erode. Additionally, unintended loss or exposure of private data, insufficient security or privacy resources leading to cybersecurity incidents, and negative newsworthy events that are not communicated promptly can also contribute to a lack of digital trust.
Interviewer: “In light of recent data breaches involving major companies, which of these events would most significantly affect your trust in a company, and why?”
Candidate: “I believe the data breach involving the online web portal system, which compromised over three billion user accounts, would most significantly impact my trust. The sheer scale of the breach indicates vulnerabilities in security protocols that could have been mitigated with more robust measures. It raises concerns not just about data protection but also about the company’s transparency and response to such incidents. Trust in a company is built on the assurance that personal information is secure, and a breach of this magnitude severely undermines that confidence.”
Digital trust is influenced by multiple factors, often tied to how secure, transparent, and ethical digital interactions are. For instance, consider these scenarios:
Credit Card Skimming: Discovering that your credit card has been skimmed at your favourite gas station, with fraudulent purchases made, can severely impact your trust in both the establishment and your card provider.
Unexpected Charges: Finding a $4,500 charge for a water purification system you never ordered can be alarming. While quick action by the credit card company in reversing the charge helps restore some trust, the incident still leaves a mark.
Biometric Data Requests: When boarding an international flight, being asked to look into a camera instead of presenting a boarding pass can raise concerns about data privacy—especially if passengers are unaware of how their biometric data is stored or used.
Each of these experiences touches on key aspects of digital trust: data security, privacy, transparency, and how quickly issues are resolved when things go wrong.
Elements of Digital Trust
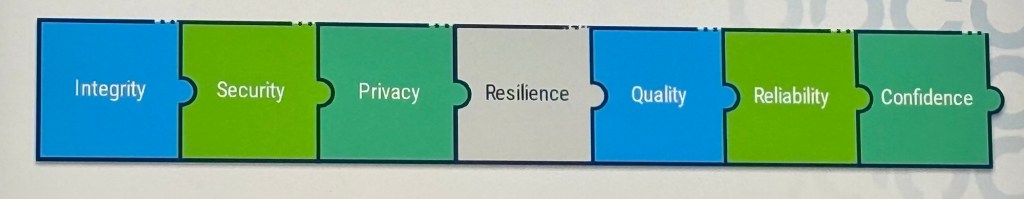
A. Resilience: is the ability of a system or network to resist failure or recover quickly from disruptions, usually with minimal noticeable effects. This requires organisations to have a common understanding of their priorities and objectives. They can then anticipate, prepare, respond, and adapt to changes or disruptions.
B. Integrity: Integrity involves safeguarding against the improper modification or destruction of information, ensuring non-repudiation and authenticity.
C. Quality: The organisation’s information about digital trust meets certain quality criteria. This is supported by both intrinsic quality (the extent to which the information is accurate, objective, and reputable) and contextual quality (the extent to which the information outcomes are relevant, complete, current, appropriate, consistent, understandable, agile, and easy to interpret). Is facial recognition appropriate at airports?
D. Reliability: Reliability refers to how consistently and accurately a company can carry out its required functions under specific conditions over a defined period of time, ensuring that the processes yield the same results each time.
Digital Trust Elements with Descriptions and Real-Time Examples
Privacy: The right of an individual to trust that others will appropriately and respectfully use, store, share, and dispose of his/her personal and sensitive information within the context and according to the purposes for which it was collected or derived.
Real-Time Example: Social media platforms like Facebook managing user data and ensuring it is not shared without consent.
Integrity: Guarding against improper information modification or destruction and ensuring information non-repudiation and authenticity.
Real-Time Example: Banking systems ensuring that transaction data cannot be altered once processed.
Resilience: The ability of a system or network to resist failure or recover quickly from any disruption, usually with minimal recognizable effect.
Real-Time Example: Cloud service providers like AWS maintaining uptime during server failures through redundancy and failover systems.
Quality: The organization’s information pertaining to digital trust meets certain quality criteria, supported by intrinsic and contextual quality.
Real-Time Example: E-commerce websites like Amazon ensuring accurate product descriptions and customer reviews.
Availability & Security: The extent to which information is accessible when needed and secured, with access restricted to those entitled and needing it.
Real-Time Example: Online banking services ensuring secure and continuous access to account information for authorized users.
Trust: The faith or belief that one will act in a right, proper, or effective way.
Real-Time Example: Customers trusting an online payment gateway like PayPal to securely process transactions.
Reliability: The ability of a company to perform its required functions accurately and reproducibly under stated conditions for a specified period of time.
Real-Time Example: Google Search consistently providing accurate search results quickly and reliably.
Digital Trust Concerns by Organization Type
Digital trust is a critical factor for all organizations delivering digital services, but the specific concerns and priorities vary by sector. Below is an analysis of the primary digital trust concerns for each of the three entity types described: a government tax agency, a global luxury hotel chain, and a global banking system.
Government Tax Collection and Management Agency
Key Digital Trust Concerns:
- Data Security and Privacy: Tax agencies handle highly sensitive personal and financial data. Citizens are concerned about the security of their data, fearing breaches or misuse by unauthorized parties. Robust digital identity verification and secure authentication are essential to prevent fraud and unauthorized access.
- Accessibility and Inclusivity: As tax services become increasingly digital, there is a risk of excluding vulnerable groups (e.g., the elderly, disabled, or those with limited digital literacy or internet access). These groups may lose trust if they cannot easily access or use online tax services.
- Transparency and Assurance: Taxpayers need clear confirmation that their submissions (e.g., tax returns, payments) have been received and processed. Lack of transparency or poor user experience can erode trust.
- Impersonal Experience: Digitalization can make interactions feel impersonal, potentially alienating users who value human support or reassurance.
- Legal Compliance and Confidentiality: Trust is grounded in the legal obligation of tax agencies to protect taxpayer data and use it only as permitted by law.
Fraud prevention is a top priority for digital government services… Governments can harness digital trust to enhance service delivery, protect citizens’ data, and foster trust in digital public services.
Global Luxury Hotel Chain
Key Digital Trust Concerns:
- Personal Data Protection: Hotels collect and store vast amounts of sensitive guest data (passport details, payment information, preferences). Guests are increasingly wary of how their data is handled, who has access, and what happens in the event of a breach.
- Cybersecurity Threats: The hospitality industry is a prime target for cyberattacks due to the high value of personal and financial data and multiple points of vulnerability (reservation systems, Wi-Fi, third-party providers).
- Transparency and Control: Guests want to know where their data is going, who can access it, and how long it is retained. Lack of clear communication undermines trust.
- Reputation Management: A single data breach can cause significant reputational damage, financial loss, and erode guest trust, which is crucial for brand loyalty in luxury hospitality.
- Balancing Personalization and Privacy: While guests appreciate personalized experiences, they are increasingly concerned about the extent of data collection and potential overreach.
- Third-Party Risks: Reliance on external vendors for services (e.g., digital check-in, payment processing) introduces additional security risks that may be outside the hotel’s direct control.
Travelers are asking harder questions: Where is my data going? Who has access? What happens if something goes wrong? And when hotels can’t answer clearly, it’s not just guest confidence that suffers, but also the hotel’s own reputational standing.
Global Banking System
Key Digital Trust Concerns:
- Data Privacy and Security: Banks are entrusted with highly sensitive financial and personal data. Customers expect strong safeguards against breaches, fraud, and misuse.
- Transparency: Customers, especially younger generations, demand clarity on how their data is used, stored, and shared. Lack of transparency is a major reason for declining trust, particularly among Gen Z.
- Cybersecurity and Resilience: As banks adopt new technologies and open banking frameworks, the risk of cyberattacks and third-party vulnerabilities increases. Customers are concerned about the bank’s ability to protect their assets and information in this evolving landscape.
- Regulatory Compliance: Trust is reinforced when banks adhere to strict legal and regulatory standards for consumer protection, privacy, and data management
- Incident Response: A single breach can erode years of trust. Customers expect prompt, transparent communication and effective remediation in the event of a security incident.
- Generational Trust Gap: While older customers tend to trust banks more, younger customers (Gen Z) are notably less trusting, requiring banks to adapt their engagement and security strategies to win over this demographic.
A single data breach can erode years of trust that banks painstakingly built with customers. Our research shows that 62% of customers lose confidence in their bank after a breach, and 43% choose to stop engaging altogether.
Data collection
First-party data refers to data that a company collects directly from its own customers. This is information gathered through the company’s own channels, such as its website, app, or customer surveys. Since this data comes straight from the source, it’s generally considered the most reliable and relevant for that business.
• Second-party data is essentially someone else’s first-party data that is shared directly with another organization. In this case, the original company collects the data from its customers and then shares it with a trusted partner. This allows the receiving company to access high-quality data that it didn’t collect itself, but still comes from a direct customer relationship.
• Third-party data is collected by companies that are not directly involved in the original customer transaction. These companies aggregate data from various sources and then sell or share it with others. As a result, third-party data is broader but may be less accurate or relevant compared to first-party or second-party data.
Digital Peers
Digital peers are two or more stakeholders engaged in a digital relationship. Many digital interactions occur between two parties, including individuals, groups, or organisations with similar characteristics and status. Examples of digital peer interactions include communication between two friends on a messaging app, sharing pictures with a group on a social media platform, and a parent sending money to their child through a fund transfer system. Donating money through a crowdfunding site is another example.
Relationships
Here is an explanation of each of these relationships:
Business to Business (B2B): This relationship involves transactions between two businesses. Companies sell products or services to other companies, such as a manufacturer selling goods to a wholesaler, or a wholesaler selling to a retailer.
B2B Definition: B2B refers to communications, interactions, and transactions between companies with digital identities.
B2B Participants: Service providers, wholesalers, retailers, and other companies along the digital supply chain.
– Purchasing data, outsourcing services, and paying for consulting services.
Business to Consumer (B2C): In this model, businesses sell products or services directly to individual consumers. Examples include online retailers, supermarkets, and service providers like salons.
This relationship refers to selling/buying or providing products and services directly between a company and its consumer or the end-user of its products and services.
– Purchasing household items, music or e-books from an online retailer
– Signing loan documents using a contract signing service
– Using food delivery services or ordering groceries online
Business to Employee (B2E): This refers to the relationship between a business and its employees. It includes internal services, benefits, and communications that a company provides to its workforce to enhance productivity and satisfaction.
Business to Government (B2G): B2G relationships involve businesses providing goods or services to government entities. This could include IT services, construction projects, or office supplies contracted by government departments.
Government to Constituent (G2C): This relationship represents the interaction between government bodies and the public. Services like issuing passports, collecting taxes, or providing public welfare benefits fall under G2C.
Government to Government (G2G): G2G relationships occur between different government agencies or levels of government. This includes collaboration on policies, sharing resources, or joint projects between departments or countries.
Peer to Peer (P2P): P2P refers to a decentralized network where individuals interact directly with each other to exchange goods, services, or information. Examples include file-sharing platforms, ride-sharing services, and peer-to-peer lending.
Explanation of Digital Trust Stakeholders
The diagram titled “Digital Trust Stakeholders” illustrates the key participants in a digital trust ecosystem and how they interact through proxy technologies. Here’s a breakdown of each stakeholder and their roles, with practical examples:
Service/Product/Information Provider
- This entity supplies digital services, products, or information.
- Example: A cloud storage company like Google Drive, which provides online file storage and sharing services.
Service/Product/Information Consumer
- This is the end-user or organization that consumes the digital service, product, or information.
- Example: An individual user or a business that uses Google Drive to store and share documents.
Third Party
- These are external entities that facilitate, verify, or enhance trust in the digital transaction or interaction.
- Example: A cybersecurity firm that audits Google Drive’s security measures, or a payment gateway like PayPal that processes transactions between a consumer and an e-commerce provider.
Digital Peer
- Digital peers are other users or systems that interact directly with the consumer, often in a decentralized or peer-to-peer context.
- Example: In a file-sharing platform like BitTorrent, each participant is both a provider and consumer, acting as digital peers to one another.
Proxy Technologies
- These are the technological solutions that mediate, secure, and facilitate interactions between all stakeholders.
- Examples:
- Encryption protocols that secure data transfer between a provider and consumer.
- Blockchain technology that verifies transactions without a central authority.
- Identity management systems that authenticate users before granting access to services.
How the Stakeholders Interact
- The Service/Product/Information Provider interacts with the Consumer to deliver digital services or products, often relying on Proxy Technologies to ensure secure, reliable, and private exchanges.
- Third Parties can audit, certify, or provide additional security or compliance assurance, building further trust between providers and consumers.
- Digital Peers interact directly, often using proxy technologies to ensure secure and trustworthy peer-to-peer exchanges.
- All these interactions are underpinned by proxy technologies that enable trust through mechanisms like authentication, encryption, and compliance monitoring[1][2].
Real-World Scenario
Consider an online banking application:
- The bank is the Service/Product Provider.
- The customer is the Consumer.
- A third-party payment processor (like Visa or Mastercard) ensures secure transactions.
- Digital peers could be other customers transferring money to each other.
- Proxy technologies include secure login systems (multi-factor authentication), encryption, and regulatory compliance tools.
From the provider’s perspective, building a trustworthy relationship involves ensuring that the consumer provides accurate, complete, valid, and consistent information. Additionally, the provider should disclose the necessary information to obtain the intended goods or services. Furthermore, the provider must assume that the enterprise will honour and maintain a fiduciary duty for this information.
The consumer perspective on digital trust encompasses several critical elements that influence their confidence in businesses and digital platforms.
Quality: Consumers expect high-quality products and services that perform reliably, meeting or surpassing their expectations.
Security and Privacy: Protecting personal data and ensuring secure transactions are paramount. Consumers are increasingly concerned about how their information is handled, expecting robust security measures.
Expectations for Digital Trust: Trust is built through consistent, positive experiences. Consumers look for brands that demonstrate reliability, competence, and clear communication.
Availability: Continuous and uninterrupted access to digital services is crucial. Downtimes or service interruptions can erode consumer trust.
Resiliency: Consumers value organisations that can quickly recover from disruptions, ensuring minimal impact on service and data integrity.
Transparency and Honesty: Open communication about business practices, data usage, and potential issues fosters trust. Honesty in advertising, service delivery, and customer interactions is key.
Ethics and Integrity: Ethical business practices and strong moral principles are essential. Consumers prefer brands that demonstrate integrity in every aspect of their operations.
From the consumer perspective, organisations build digital trust under the following conditions:
– The enterprise is transparent, honest, and accountable.
– Privacy safeguards are in place throughout the economic life cycle.
– The products, services, or assets consumers receive meet their expectations.
– Data are used only with the consumer’s explicit consent.
– The information users rely on is available, accurate, complete, consistent, useful, relevant, and timely. Information integrity is assured.
– The enterprise operates with high ethics and integrity, offering its products or services sustainably and legally.
– The information supplied to the organisation is protected and securely disposed of when no longer needed.
– The organisation is resilient to external influences.
When an enterprise also functions as a customer in the supply chain, it should ensure that its upstream providers:
– Provide only the information necessary for the downstream provider to process a transaction or provide transactional services.
– Manage data as agreed upon by the downstream stakeholders to ensure data is appropriately secured and disposed of when no longer needed.
– Establish appropriate privileged access to deliver services and products.
Proxy technology
Proxy technologies facilitate information transfer between consumers, providers, peers, and third parties. Examples include artificial intelligence platforms, online portals, cyber-physical systems, bio-recognition devices, the Industrial Internet of Things, social media platforms, kiosks, radio frequency systems, video/livestream conferencing systems, email and calendar services, messaging applications, and document sharing sites.
Secondary Relationships
Enterprises are increasingly reliant on third-party vendors for business operations. Cloud technologies and services empower companies to seize opportunities and maintain their competitive edge in the digital landscape.
From a third-party perspective, digital trust demands effective governance of cloud computing. This involves considering critical business drivers such as:
– Optimised resource utilisation
– Cost savings
– Enhanced responsiveness
– Faster innovation cycles
– Reduced implementation time
– Enhanced resilience
Digital Activities
Digital identity/behaviour: This activity ensures that everything people or organisations do with technology online is tracked and recorded.
Digital connection: This activity takes digital behaviour one step further by linking users’ actions to standard digital collaboration tools or connections between two entities.
Digital communication: This activity involves transmitting data and information between two stakeholders in a digital relationship.
Digital interaction: This activity is the culmination of digital behaviours, relationships, and communications that have a specific outcome.
Digital transaction: This activity refers to the stakeholder-to-stakeholder exchange of information (e.g., payment) for a product or service.
Digital Trust Hierarchy
Use or avoid-Stakeholders’ choice to digital tech for tasks/communication.
Necessity-This level refers to a stakeholder leveraging a digital platform to complete tasks when a manual option may not be efficient or feasible.
Vulnerability based-Selecting digital activities that help identify and avoid digital communication vulnerabilities or inefficiencies associated with a new relationship.
Experience and confidence-Stakeholders feel comfortable engaging in digital interactions based on previous experiences, favorable outcomes, brand reputations, behaviors and communications.
Established and valued-Stakeholder trust in provider/consumer relationship for consistent value and minimal risk.
Digital Trust Framework
The Digital Transformation Effort Framework (DTEF) affects various stakeholders, including IT experts who support information systems and marketing professionals who promote and protect the brand. Third-party providers, companies that use them, and others are also impacted by the DTEF. Since most companies have digital footprints, and most employees may inadvertently contribute to them, cybersecurity, risk management, legal, audit, compliance, privacy, business continuity, quality control, human resources, IT, marketing, communications, procurement, and third-party vendor management are all areas that are affected by the DTEF.
Digital trust provides assurance and gives the cost effective security, optimising the use of resources and the legal environment being compliant with laws and regulations.
Digital trust is imperative for businesses in today’s digital landscape. Senior management should develop and prioritise a digital trust strategy to maintain a competitive edge. This strategy should cascade down to all internal stakeholders, including business management, marketing, IT management, HR, internal audit, and risk and compliance teams. Each stakeholder plays a vital role in meeting stakeholder and customer needs by translating business goals into digital trust goals and establishing a trustworthy digital footprint.
Strategy and come up with roadmap, highest lead CEO take it forward
There is goal cascading from governance to management to ensure the strategic goals are met.
The DTEF (Digital Trust Ecosystem Framework) avoids linear thinking pitfalls by using systems thinking principles.
Systems thinking focuses on components, interconnections, delays, boundaries, limits, and feedback loops to create synergy within the digital world.
Examining digital trust solely from a people, process, technology, and organisation perspective is ineffective.
Enterprises tend to view problems simplistically, with straight-line cause and effect, although intricate and indirect relationships create the problem.
Trust is built on accurate information, transparent data-sharing practices, trustworthy third parties, and feedback loops. Digitally trustworthy enterprises provide accurate and consistent information. Inaccurate information can cause harm, damaging the relationship between parties and affecting future dealings. To maintain digital trust, companies should provide accurate, up-to-date information, solicit consumer feedback, and conduct regular assessments.
Which of the following DTEF components defines the steps needed to demonstrate that a practice has been implemented?
Activities
Trust Factors
Domains
The correct answer is Activities.
Reason: In the context of DTEF (Digital Trust and Engagement Framework), Activities refer to the specific actions or steps that are necessary to implement and demonstrate a particular practice effectively. They provide a clear sequence of tasks that can be observed, measured, and evaluated to confirm that the practice has been put into action.
Trust Factors are elements that influence the perception of trust but do not define implementation steps.
Domains represent broad categories or areas within the framework, which encompass multiple practices and activities but are not focused on specific implementation steps.
The correct answer is:
B. Restrictive processes and unquestioned conformance can gradually replace critical thinking.
Explanation:
When addressing the People node within an organisational context, the focus is on human behaviour, mindset, and interactions. A potential conflict arises when restrictive processes and unquestioned conformance diminish critical thinking among employees. This stifles innovation, reduces problem-solving capabilities, and leads to a rigid work culture where employees follow procedures without understanding the rationale or considering improvements.
On the other hand:
A (Processes not designed or executed properly) pertains more to process-related issues rather than people-specific conflicts.
C (Employees using inappropriate tools) relates to technology or resource issues rather than directly to the people aspect.
Hence, option B is the most relevant conflict when focusing on the People node.
An organization determines that their overall process maturity is low. As a result, they decide to address the Process node first in their digital trust efforts. What DTEF domains would be the most appropriate to focus on?
People, Organization, Technology
Direct and Monitor, Emergence, Enabling and Support
Culture, Architecture, Human Factors
The correct answer is:
Direct and Monitor, Emergence, Enabling and Support
Reason:
When an organisation identifies that its overall process maturity is low, focusing on improving and structuring processes becomes critical. The domains within the Digital Trust and Enablement Framework (DTEF) that are most appropriate to address this are:
Direct and Monitor: This domain helps establish governance mechanisms, setting objectives, and ensuring that processes are aligned with business goals and regulatory requirements.
Emergence: This domain focuses on adaptability and responsiveness in processes, enabling the organisation to evolve with changing business and technological environments.
Enabling and Support: This domain ensures that the necessary resources, tools, and support mechanisms are in place to facilitate effective process implementation and continuous improvement.
When an enterprise also functions as the customer in the supply chain (e.g., the downstream customer of the second-party and third-party services), that enterprise should ensure that the upstream providers:
Immediately notify all stakeholders and disclose all potential risks to customers or consumers.
Identify, create and test all continuity or disaster recovery plans.
Manage data as agreed upon by the downstream stakeholders to ensure data are appropriately secured and disposed of when no longer needed.
While implementing technologies to support digital trust, organizations must train staff to use different tools and monitoring utilities to verify that it functions appropriately, therefore linking the Technology and People nodes. Which of the following is the most appropriate domain that links these nodes?
Direct and Monitor
Architecture
Human Factors
The scenario describes how organisations must train their staff to use various tools and monitoring utilities effectively. This involves both the technological aspect (tools and monitoring systems) and the people aspect (staff training and usage). The domain that appropriately links these two nodes—Technology and People—is Human Factors.
Human Factors focuses on understanding how people interact with technology and systems, ensuring that technologies are user-friendly, safe, and effective. This includes training, usability, ergonomics, and how human behaviour impacts system performance.
Option A: Direct and Monitor typically refers to governance activities like oversight and compliance, not directly linked to the interaction between people and technology.
Option B: Architecture deals with the structural design of systems, which is more technical and doesn’t primarily focus on the people aspect.
The Organization node is a network of people interacting via processes and technology. This node includes:
Permanent associates, external partners, consultants, contractors, third-party vendors, customers
Cameras, vehicles, home automation, smartphones, websites, kiosks, loT devices, sensors
Culture, Emergence, Human Factors, Direct and Monitor, Enabling and Support, Architecture
Activities are listed in a specific domain in the DTEF. Why is it important to note that an activity may be related to other domains and practices?
A change in one domain may impact another domain.
Activities are directly related to meeting cybersecurity and privacy requirements and may affect other domains and practices.
Activities do not have relationships with other domains and should be considered only in the domain and practice they are in.
Microsoft Entra solution areas include:
1. Establish Zero Trust Access Controls: Implementing security measures that ensure only verified users can access resources, based on their identity and context.
2. Secure Access for Employees: Providing secure access mechanisms for internal employees to company resources.
3. Identity and Access Management (IAM): Managing user identities and their access to resources within an organisation.
4. Secure Access for Customers/Partners: Ensuring secure access for external users, such as customers and partners, to company resources.
5. Customer/External IAM: Managing identities and access for external stakeholders.
6. Zero Trust Network Access: Applying Zero Trust principles to network access, ensuring secure and verified access to network resources.
7. Secure Web Gateway: Protecting web access by filtering and securing internet traffic.
8. Identity Governance and Administration: Managing and governing user identities and access rights.
9. Advanced Identity Protection: Implementing advanced security measures to protect user identities.
10. Verifiable Credentials: Using digital credentials that can be verified to ensure authenticity.
11. Accelerate with Generative AI Capabilities and Skills: Leveraging AI to enhance identity and access management processes.
12. Secure Access in Any Cloud: Ensuring secure access to resources across various cloud environments.
13. Workload IAM: Managing identity and access for workloads and applications in cloud environments.
“Secure access” and includes “Onboard users,” which involves adding both employees and guests to a directory. “Govern access” features automated access rights granting, self-service access requests for additional needs, and just-in-time access with alerts and approval workflows to safeguard critical resources. It also mentions access recertification to minimise risk and lifecycle automation for managing user transitions (joiner/mover/leaver). There should be continuous risk assessment and automation, threat intelligence, and telemetry. The Zero Trust model with an adaptive risk-based access policy.
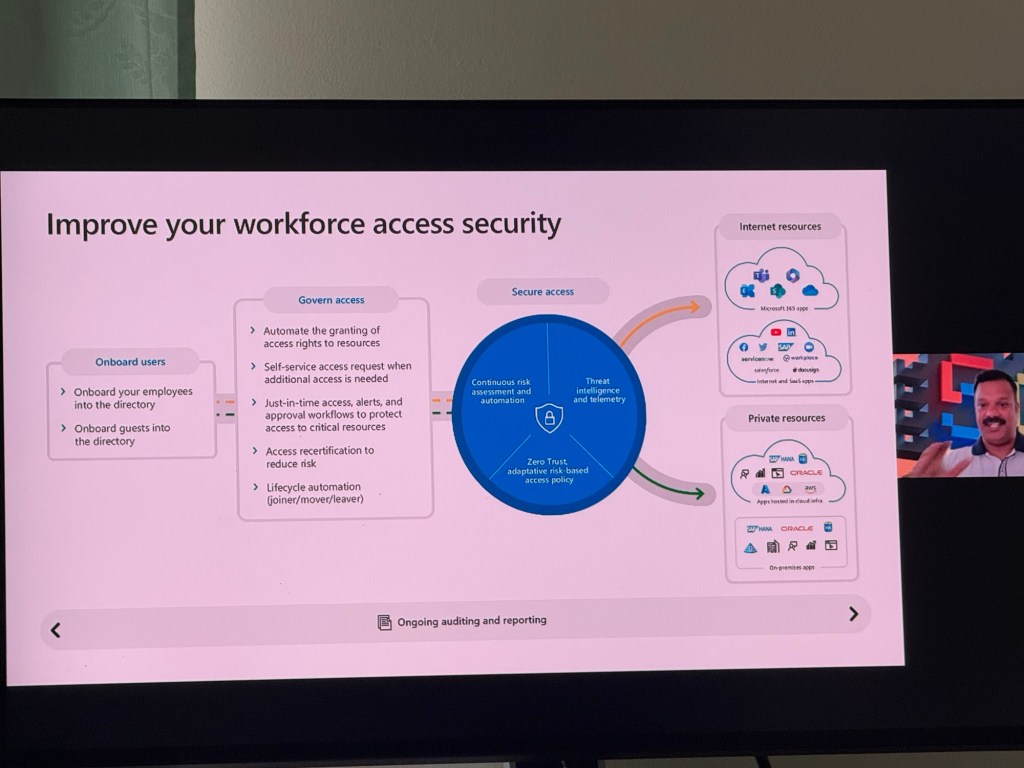
All workflow has to be done automatically without the It team having to configure a script. On governance is in place, secure channel access/on-premises access like legitimate SSO, no anomaly or risk score associated then there can be zero trust implemented.
The process involves enhancing the onboarding and lifecycle management for both employees and external users. For employees, it includes synchronising users from the authoritative system of record, simplifying and customising the identity verification process, and using Face Check for real-time high assurance facial verifications. These capabilities can also be extended to external users. Access governance is automated through join/move/leave events and the initial granting of access rights, known as birthright assignment. This process can be implemented using systems like Microsoft Entra ID and Active Directory, with lifecycle automation requiring additional licensing.
Provision directly to AD or intra ID.
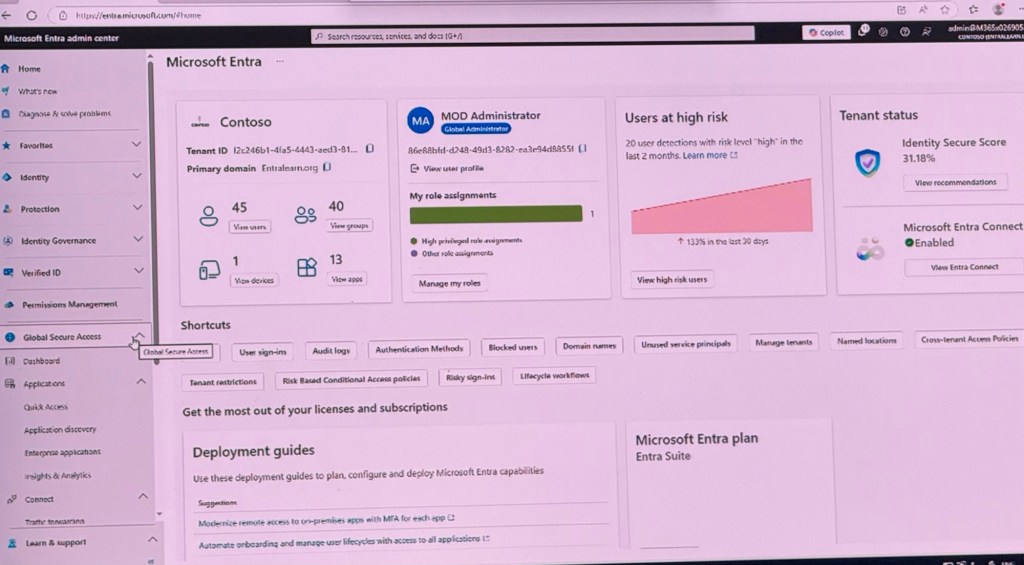
The Microsoft Entra admin centre, a platform used for managing identity and access services. It shows various sections and features available within the centre, such as:
- Search Resources, Services, and Docs: A search bar for finding specific resources or services.
- Home: The main dashboard where users can access different sections.
- What’s New: Updates and new features available in the platform.
- Favourites: A section for saving frequently used resources.
- Identity: Includes features like Identity Governance, Verified ID, and Permissions Management.
- Protection: Focuses on security aspects such as Global Secure Access.
- Applications: Manages applications, including quick access and discovery.
- Insights & Analytics: Provides data and insights related to identity and access.
- Connect: Likely refers to Microsoft Entra Connect for integrating on-premises and cloud services.
- Learn & Support: Offers resources for learning and support.
The screenshot also displays specific user information, such as:
- Contoso MA MOD Administrator: The user’s role and organisation.
- Tenant ID: A unique identifier for the tenant.
- Primary Domain: The main domain associated with the tenant.
Additionally, it shows various management options like user profiles, role assignments, device management, and security settings such as user sign-ins, audit logs, and authentication methods. There are also sections for managing high-risk users, tenant status, and identity secure scores. The image includes deployment guides and suggestions for modernising remote access and managing user lifecycles.
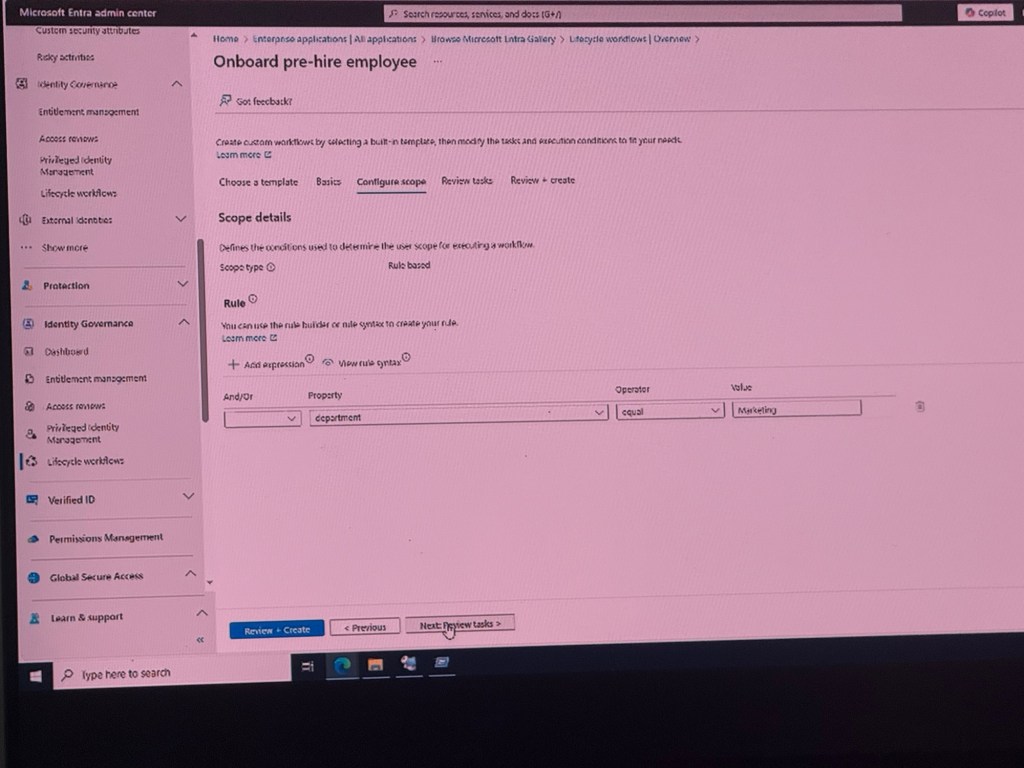
The Microsoft Entra admin centre offers a range of features for managing identity and access. It includes custom security attributes, identity connection, entitlement management, and privileged identity management. The centre also supports lifecycle workien, external identity protection, identity governance, and a dashboard for monitoring. It provides permissions management, global secure access, and resources for learning and support. Users can onboard pre-hire employees by selecting a template and modifying tasks and execution conditions to fit their needs. The centre allows for defining user scope conditions, creating rules using rule-based syntax, and applying access restrictions based on properties like department.
Birthright access is common among all the employees of the organisation.
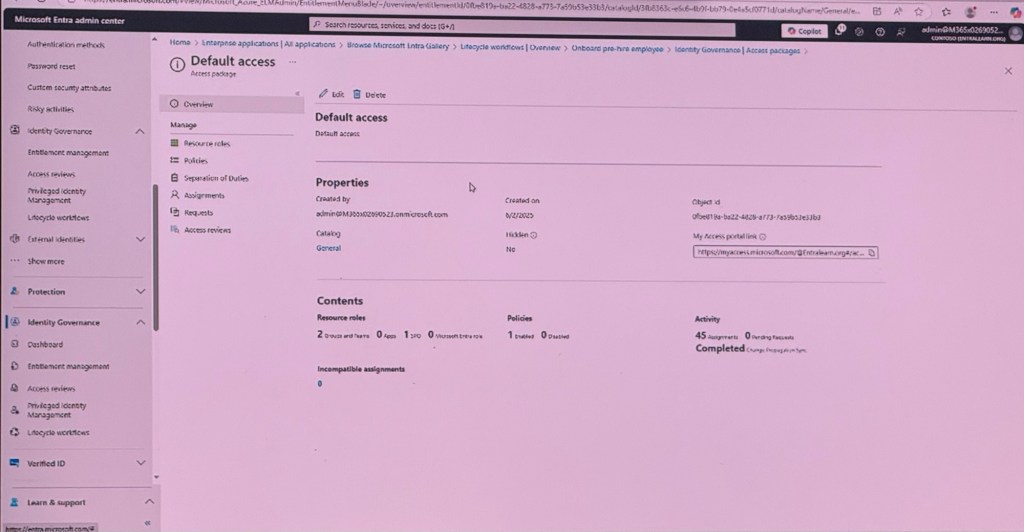
Govern access to sensitive resources.
Scenario 2b: Just-in-time governed access to sensitive resources.
– Users can activate sensitive resources on-demand.
– An approval workflow is in place for privileged access.
– Privileges expire after a specified interval.
– Sensitive access is periodically recertified.
Ensure least-privileged access.
The process involves modernising remote access to on-premises resources by implementing Multi-Factor Authentication (MFA) for each resource. This ensures secure and quick access to private resources. The setup includes using Microsoft Entra ID and Microsoft Entra Private Access for quick access through a trusted network route. The insecure port number is 445.
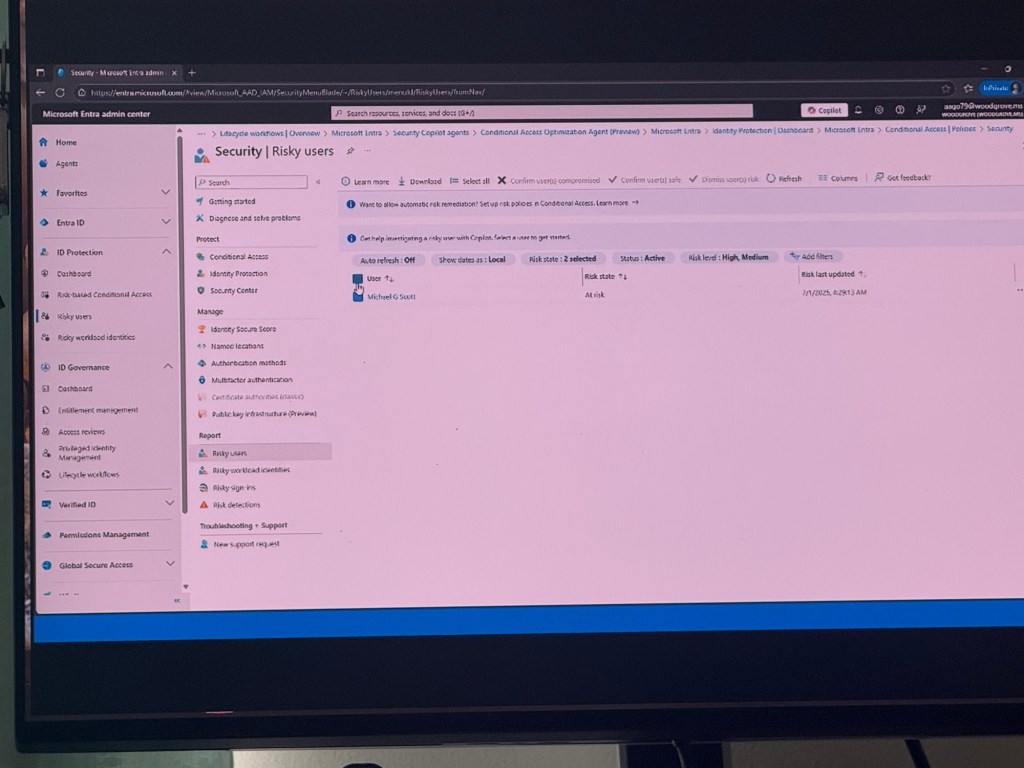
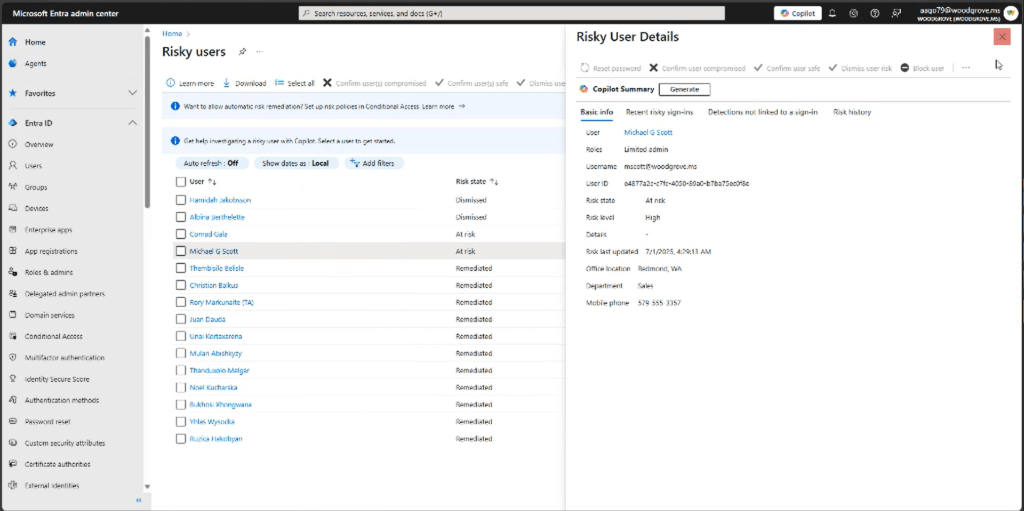
The dashboard provides a comprehensive view of security settings, including risky users and conditional access policies.
- User Verification: Users can be verified by email or SMS to confirm their identity, which is crucial for security.
- Risk Management: The dashboard highlights risky users, allowing for the selection and management of these risks. It categorises risks as high, medium, or low, with options to filter and refresh the list.
- Identity Protection: It includes features like identity protection, which likely involves monitoring and safeguarding user identities against potential threats.
- Security Centre: This section is likely for managing security policies and settings, ensuring that the organization’s security measures are up-to-date.
- Risk Detection and Reporting: The dashboard includes risk detection capabilities and reporting features, allowing for the identification and documentation of security incidents.
- Support and Troubleshooting: Users can request new support and troubleshoot issues related to security and identity management.
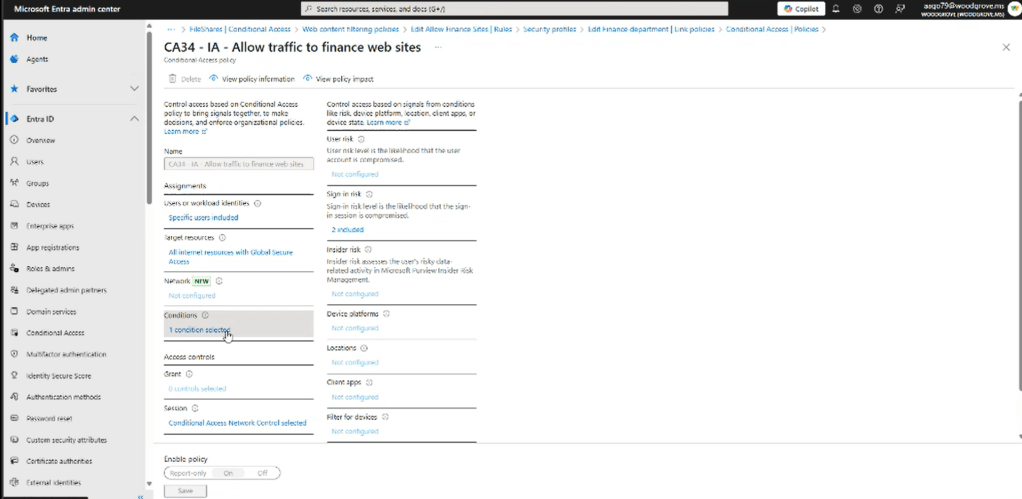
GenAI solution for co-pilot can be integrated using plug in.
Ask: Show high risky users in my tenant.