An audit is to attest to an entity’s IT process and control designs or/and operating effectiveness. The process of reviewing a system for compliance against a standard or baseline.
Examples: audits of security controls, configuration baselines, and financial records.
Control testing is the most. How IT audit is executed and completed. We have access cards to prevent unauthorised access to the data centres.
How: testing and operating effectiveness with evidence.
Why: whether effective or not effective.
Audit life cycle: planning, fieldwork (testing falls into), reporting.
IT control testing
Pre planning administrations, understanding clients and their process, defining scope and objectives, defining your scope and objectives, creating planning memos, procedures and risk assessments, client/team communications
Execution/fieldwork: creating and managing evidence requests, sample sizes and population, conducting meetings and work sessions, examining evidences/deviations in audit work papers, reviewing and approving work papers, client/team communications
Reporting: Assessing control findings, drafting audit reporting, creating lessons learnt, summary memos and wrap up documentations, stakeholders reviews and approvals, client/team communications
What is IT audit control testing?
Walkthrough with the client (meeting/interview) to go through the control processes and go with any questions with them like what kind of evidence they can support, and even have them show you how control works. After this the auditing team expresses their understanding of the controls. Once the evidence is obtained the auditor control tests by evaluating (design/operation). Once done the auditor and manager review the processes.
How are controls tested?
Step 1: Having a walkthrough.
Step 2: Conduct test scripts via audit testing methods on procedures with sufficient and appropriate evidence.
Step 3: Documentation result and conclude on the controls’ design effectiveness and/or operating effectiveness for the audit period.
Procedures
They are specific instructions outlined in a work paper/lead sheet which the auditor uses to follow in testing a control. Steps may include:
- Steps in obtaining specific evidences relevant to control.
- Steps in evaluating the design and implementation of the controls
- Steps in evaluating the operating effectiveness of the control.
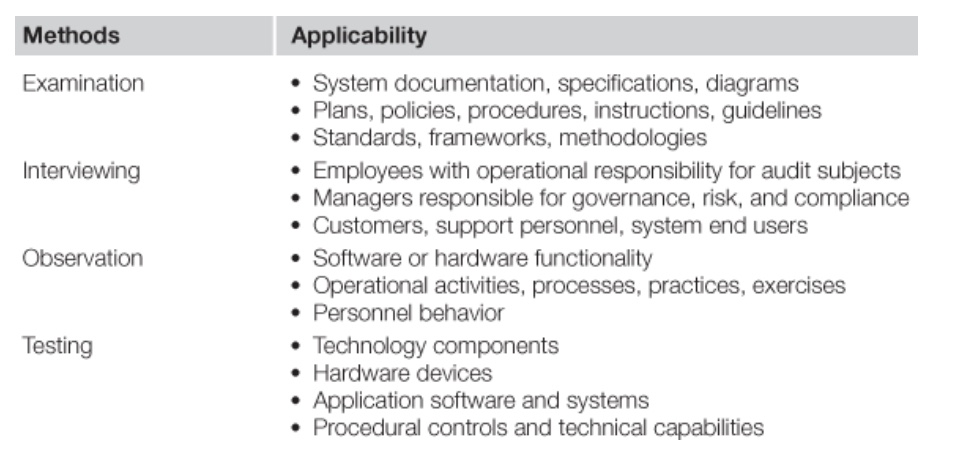
Testing methods
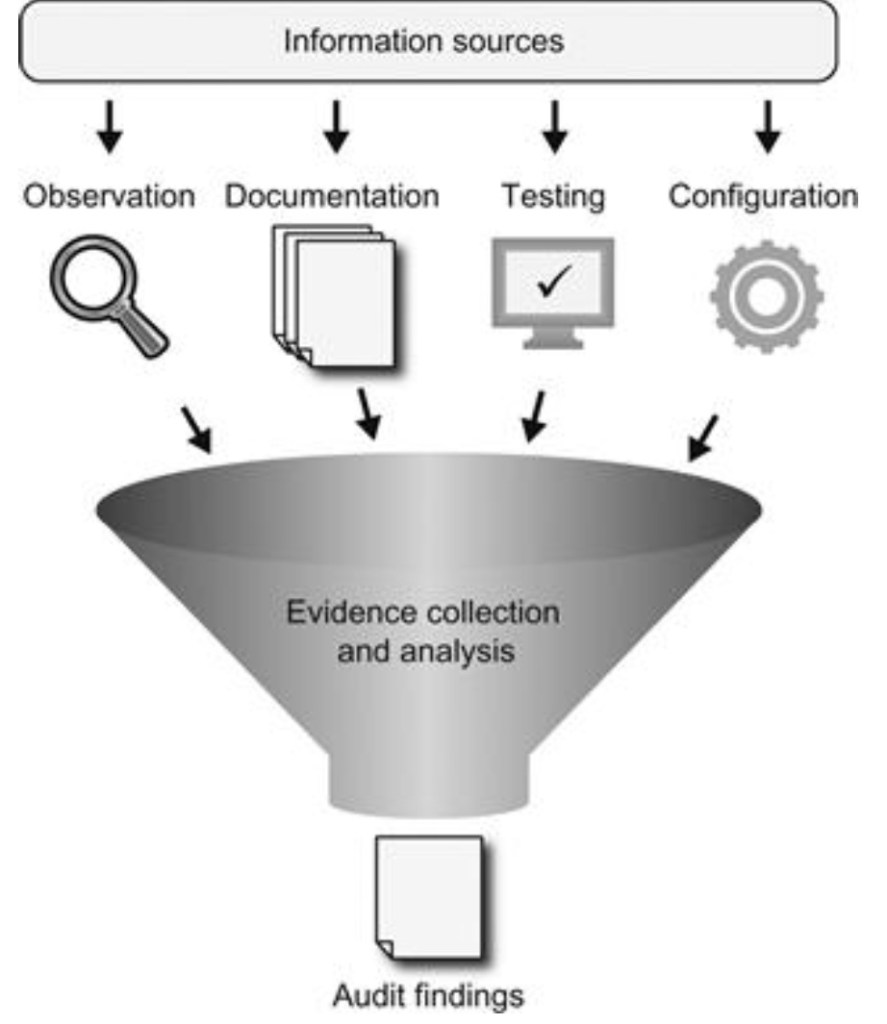
Observation is the audit procedure to attest control by observing/viewing the control performer executing the controls
Examination is the inspection of relevant audit evidence (screenshot, documents, logs, user, listings, etc.)
Inquiry is when the auditor asks questions to the auditor to determine the relevant information
Re-performance is the auditor independently executes the control that they are validating
Analytical is when the auditor uses Analytics and computer assisted auditing testing to determine relevant information
Basic Controls testing concepts
Design effectiveness is defined as evaluating the controls design and whether the control can address the risk. auditors generally test an instant or sample of one to conclude whether the control is designed and implemented properly.
Operating effectiveness is defined as evaluating the controls ability to operate for a period of time. Auditors generally obtain a population and select samples to conclude whether the control can operate effectively for the given period.
- Evidence: It is defined as a support/proof need to verify/validate that the control objective is met.
- Sufficient evidence is defined as having enough sample/multiple evidences in your control testing to validate/verify that the control objective is met. Example: The servers are patched with the security updates.
- Appropriate evidence is defined as having relevant sample/multiple evidences in your control testing to validate verify that the control objectives met.
Types of cyber and IT audit evidences
- Listing/Data extracts: List of change management tickets from system, CMDB, computer inventory assists, population for the auditor to pick/choose samples.
- Email/documents: Policy, procedures, plan, diagram, process design.
- User listings: criterial form of evidence, which users are administrators and which all have access to the system.
- Log/schedules: extracted from system databases, logs show historical activity prepared by a system used by the user.
- System configurations: codes, configurations, settings are turned on or off.
Samples versus population
Population is defined as a pool of instances/individual/objects or items that the sample is full form. Population is generally related to the evidence used in control testing.
Samples are defined as a set of instances/individual/objects or items that are selected from a population. Sampling technique include:
- statistical sampling
- Random sampling
- Systematic sampling
- Non-statistical sampling
- non-statistical sampling
- HapHazard sampling
- Block sampling
- Professional judgement
Population Frequencies
Hourly/daily, weekly/bi-weekly/monthly, bi-annually/semi-annually, multiple times a day, as needed/continuous
Exceptions
Issues and errors identified in control testing. These are documented in work papers. Anomalies that can be reasoned and explained are not exceptions.
Findings
Aggregate set of exceptions with risk that can lead to control design and/or operating effectiveness failure. These are reported on the Audit report. When number of exceptions high and impactful, audit finding may likely occur.
Control testing outcomes
Ineffective : Control is not designed and operating effectively to address the risk within the audit period.
Effective : Control is designed and implemented and/or operating effectively to address the risk within the audit period.
Effective with exceptions: Control is designed and implemented and/or operating effectively but have anomalies/exceptions.
File structure It is important to understand the overall documentation process: like where and how to document. It uses software repositories where it stores all the testing and the evidences.
- Audit file: Has the overall file repository containing the contents of the audit from planning the document, work papers, the finding report and audit report.
- Audit program: Structure within the audit file which outlines the process objectives, entity/client details, risks, controls, test procedures which the auditor will test and validate for their audit.
- Work papers: Documents which outline the results of the auditor’s control testing. Evidences are either uploaded/attached as part of the work papers. Other details like sampling, population and control details may be referred/attached.
Accessing control design
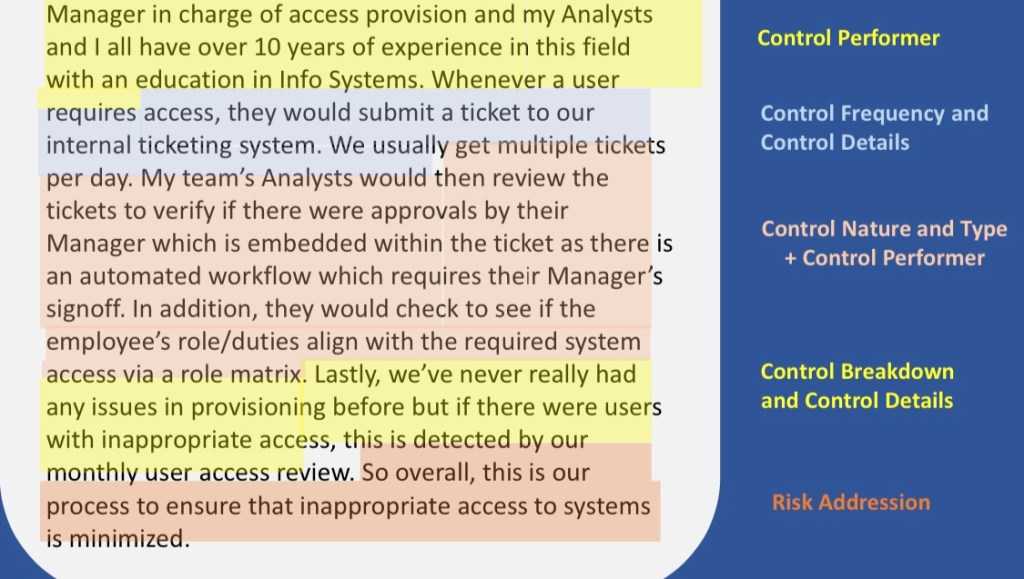
Control design factors help determine if the controls are preventive or detective (which shows that a risk has happened) so that appropriate action can be taken. The automated manual nature of the control helps determine if the control operates without human intervention. Control frequency and population will be same in most cases. Control performer looks at the background of the person who is person who is performing a control. Control breakdown how the control is broke down, what happens when control breaks down. Risk address mean whether the control will access the risk itself. We want a controller which can detect inappropriate access properly.
Popular governance frameworks such as COBIT and the Information Technology Infrastructure Library (ITIL) are largely process-oriented, while enterprise architecture and information security management frameworks align more closely to organizational descriptions or decompositions that are more technical in nature.
The Committee of Sponsoring Organizations of the Treadway Commission (COSO) defines internal control as a process “designed to provide reasonable assurance regarding the achievement of objectives” including operational effectiveness and efficiency, reliable reporting, and legal and regulatory compliance.
National Institute of Standards and Technology (NIST) in its information security guidance for federal government agencies [6]. NIST uses operational to distinguish controls implemented and performed by people. In many auditing contexts, however, “operational controls” is used to mean “internal controls” so to avoid confusion auditors and organizations prefer the more prevalent administrative–technical–physical categorization.
Overall there are many different terms and concepts. In this course, we’ve mainly went over specific concepts that can assist you as a practical fieldwork/execution guide. As you progress through the different sections, other terms/concepts will also be explained.
There are also many more concepts but these are covered in other parts of the series or outside of the course. The main idea is to provide you only the important day-day concepts in these practical guide.
• What is IT audit controls testing
• Basic controls testing concepts
Assessing Control Design
Assessing Control Operating Effectiveness
Audit Fieldwork Activities
Cyber and IT Technicals
Reporting
Control Design Factors
Prior year conclusion
Prior year exceptions/findings Prior year fraud
Prior year security breaches Complexity of control
Volume of instances/transactions Control Dependencies
Control Design performer
Years of experience, Independence, Education, Objectivity, Certifications
Control Breakdown
Resolution/Follow-up relates to if there are other controls or processes to remediate or address the control’s identified exceptions. Threshold is the limit/amount that is allowed before the control is triggered.
Risk address: The risk, control.
Operating Effectiveness
Sufficient & Appropriate Evidence that satisfies the audit period via appropriate sampling from population(s) + Testing of Procedures with auditing methods = Conclusion of the Control’s Operating Effectiveness
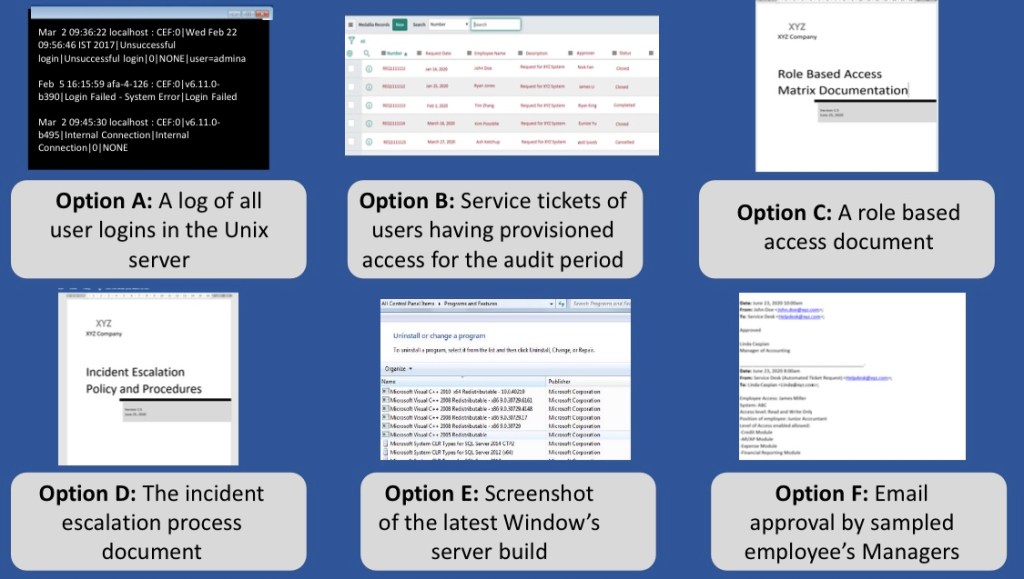
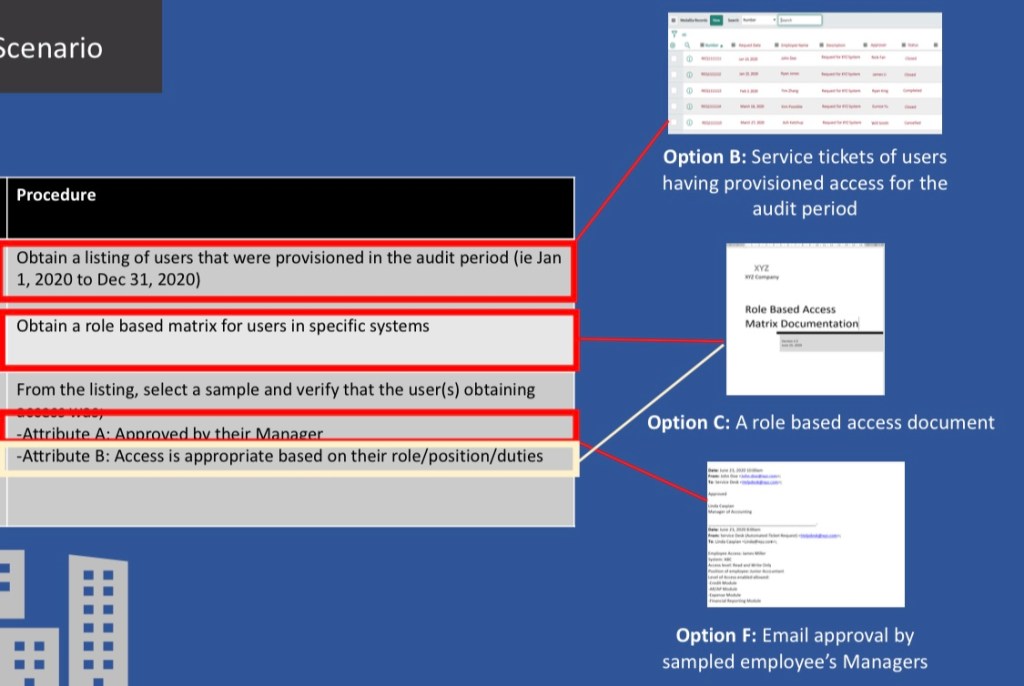
Audit procedures for access provisioning control

Sarbanes-Oxley (SOX)
Regulates public companies and their auditors; applies to all issuers of securities exchanged in US markets.
Service Organization Control (SOC)
This means that an organization that implements formal governance, risk, and compliance (GRC) models or quality assurance standards also needs an effective IT auditing capability. For many organizations the decision to establish and maintain risk management or IT governance programs is a choice, not a requirement, but such approaches are commonly viewed as best practices.
General controls include five categories: security management, access control, configuration management, segregation of duties, and contingency planning.
Document such as policies, plans, procedures, standards, guidelines, technical specifications, contracts, licenses, and service level agreements;
• interviews with organizational personnel responsible for operating or managing the subject under examination;
• direct observation of activities occurring in the organizational environment;
• applications, databases, user interfaces, and other technical components;
• performance data such as customer and supplier satisfaction ratings or quality reports produced by third parties; and
• simulated or actual control testing, modeling, or exercises.
ERP applications like SAP and databases
With solutions from SAP, retail companies get:
• More effective business decison making. Simple and intuitive user interfaces foster broad adoption, while reducing IT backlog. Business users quickly access any type of information, regardless of its source. And with SAP NetWeaver BW Accelerator technology, response times are consistently fast, independent of data volumes analyzed or question asked, allowing IT to meet the increasing demand for real-time BI embedded into business operations.
• More efficient IT, freeing up resources for innovation. The broadest solution set in the industry, combined with best-in-class capabilities, dramatically reduces the need to deal with multiple vendors. Due to inter-operability with any systems, applications or databases, investments are protected and don’t require expensive custom-integration. By providing the right level of controls with an agile infrastructure, IT can focus on managing service levels, and does not need to manage individual users.
• Faster realization of value from IT investments. Out-of-the box content and templates, across both SAP- and non- SAP data sources fosters accelerated deployments of BI solutions while significantly increasing the chance to “get it right” from the beginning, as compared to pure custom-built approaches. And alternative delivery models (e.g. on-demand, appliances) provide drastically reduced setup time and lower maintenance.
http://www.sap.com/solutions/sapbusinessobjects.
Include few topics like:
What are ITGC controls
Which are important controls in change management to be tested?
Which are important controls in access management to be tested?
What is SOD (Segregation of Duty)
Difference between production and test environment
Can a developer be tester?